Information and Communications Technologies
Gate access control system

This access control system can quickly recognize targets by using UHF band RFID tags even they are away from the detector.We developed this system for factories and facilities that are not compatible with proximity contactless cards for entry/exit systems.
Usage example
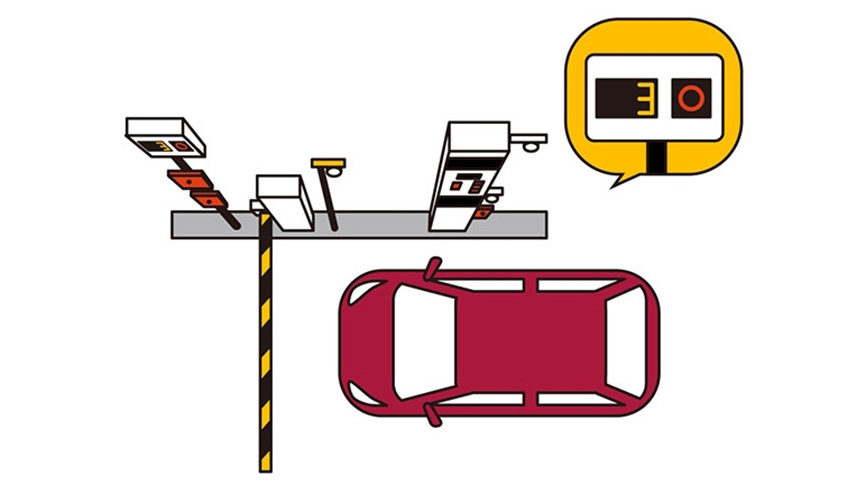
- When you hold your entrance card (with a UHF RFID tag) over the antenna at the gate, the system reads data from the entrance card.
- The expiration date is checked to prevent unauthorized entry.
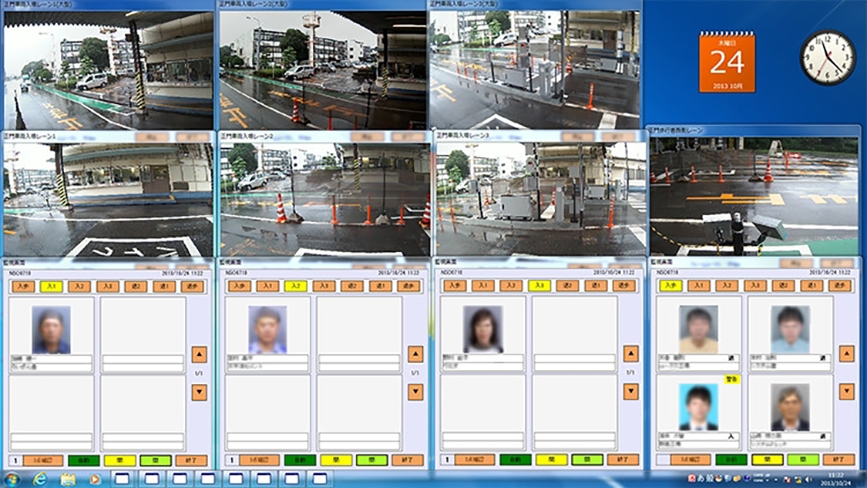
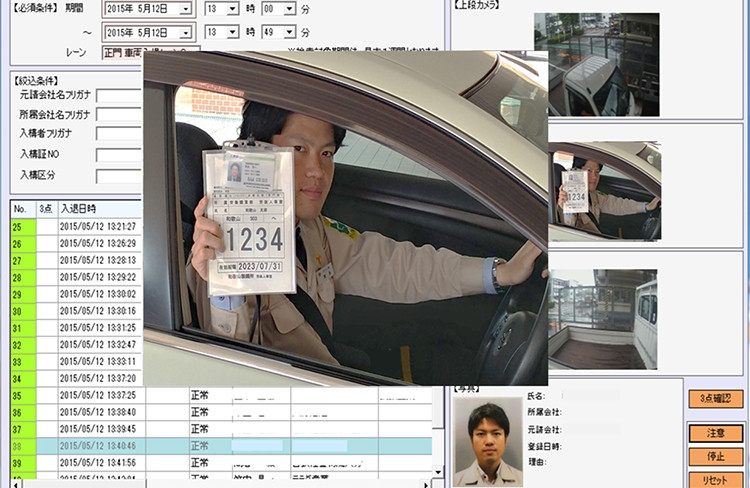
- Information on the person at the gate is displayed on the screen to help the security guard do the three-point check (identity, organization, and purpose).
- Authentication records are stored in the database and they are used for record searches, statistics, and safety confirmation after a disaster.
- No traffic jams occur due to system introduction because the edge computing processing is rapid.
Authentication results are displayed.
Benefits
High-speed processing means no traffic jams.
- The controller employs a reliable, high-speed sequencer.
- Our proprietary program significantly accelerates the processing speed.
- The system provides high simultaneous recognition performance for multiple passengers.
Dramatic improvement in gate security
- ID recognition replaces visual inspection.
- Support for touch panel monitors and tablets improves security flexibility.
- You can grasp past entrance/exit situations at a glance and still images are available as records, including head-and-shoulders shots.
Three-point check on the surveillance monitor (display of head-and-shoulders shots and recognition results)
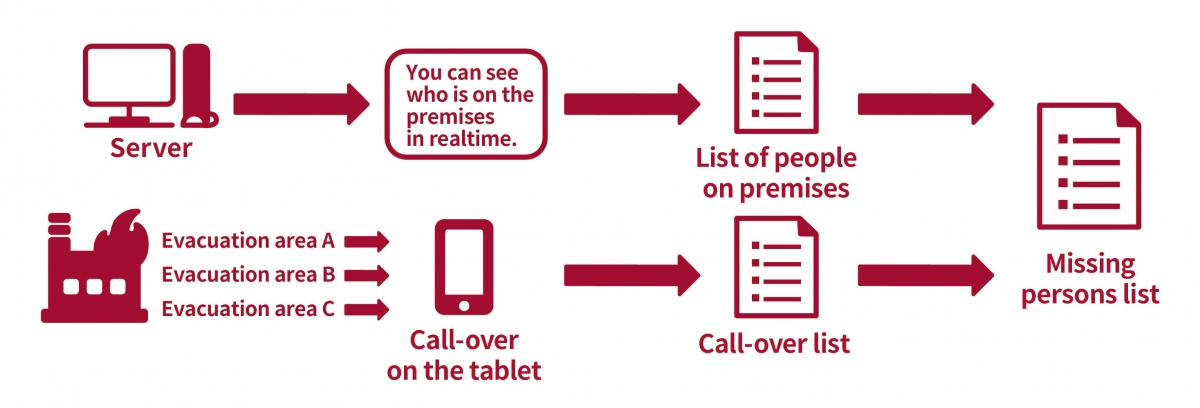
The safety confirmation function also serves a purpose for disaster control.
- You can see who is on the premises in realtime. This information can be used to confirm their safety in the event of a disaster.
- The missing persons list is output by deleting those on the call-over list from the list of people on premises.
Introduction case studies
Many clients including Nippon Steel Corporation have adopted this system.
System configuration
A variety of options allow you to build the system you need.
- Easy hardware design
- Easy system building
- Total support from introduction planning, design, setup, through to operation follow-up